
The platform was threatened with a ban after allegations of espionage and Chinese government involvement.
Read More
Amid drama and sadness, the story contains many quotes.
Read More
Kylie and Timothée haven't said anything about it.
Read More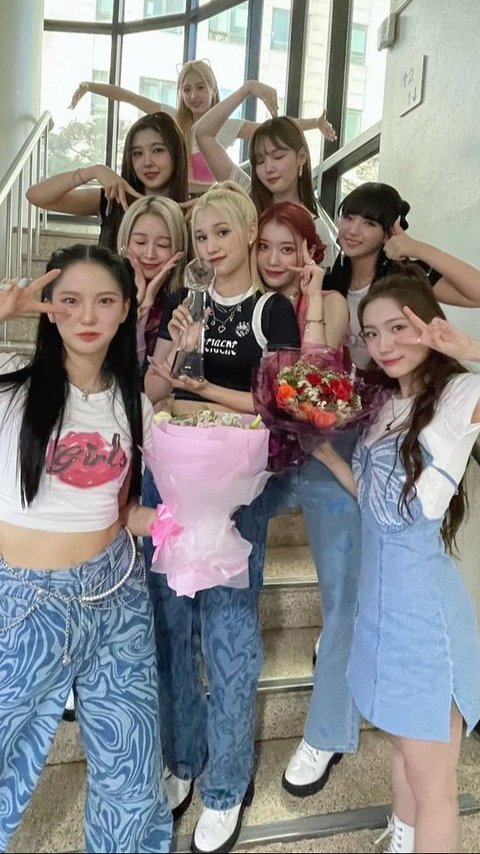
Their contract was supposed to last two years and six months.
Read More
This special event was attended by a series of popular K-Pop idols.
Read More
Do you ever hear words that make you feel small or sad? Some are mean and hurtful
Read More
The fine was levied against festival organizers following the singer's headline set.
Read More
K-pop girl group NewJeans reportedly plans to release a new music project next month.
Read More
A young man in China who is quite smart in academics was rejected by a prestigious campus.
Read More
Sending heartfelt farewell wishes is a simple but meaningful act to say goodbye to your valuable coworker, boss, or employee that leave the company.
Read More
The object claimed to be a diamond was launched in Luoyang, Henan Province, China.
Read More
In this article, we have selected some tree quotes that will inspire and deepen your appreciation for nature.
Read More
From the iconic Alamo to the mysterious inn, these haunted places in San Antonio bring us into the eerie past and supernatural encounters.
Read More
The Black Dog, a restaurant and pub in London, England, is suddenly crowded.
Read More
Dutch researchers recently reported the longest known case of SARS-CoV-2 infection.
Read More
Rain is more than just water falling from the sky. It’s a source of inspiration for many people around the world.
Read More
Here are some of the hottest girl ever appeared in Fast & Furious series.
Read More
Scorpios cherish their alone time for reflection and recharge. Plus, they make connections with those who trulys understand them.
Read More
Here are some of the best time travel movies you should add to your watch list.
Read More
Kristen Stewart movies have something action-packed for everyone.
Read More
Survival horror games are a popular genre that combines elements of horror fiction with challenging gameplay.
Read More
Let these Jurassic Park quotes inspire you to revisit the thrilling world of dinosaurs.
Read More
This surprising plan gets mixed reactions by many people.
Read More
If you are looking for some amazing offbeat destinations in Italy, here are the top 8 hidden gems in Pizza country to add to your bucket list.
Read More
The 1990s was the decade when Hollywood gave rise to many actresses who became cultural icons.
Read More